BANKING STRATEGIES
The cost of cybercrime across the world is staggering, with some estimates ranging as high as more than $22 trillion a year in direct losses and the cost to deal with the aftermath. And in the banking sectors, the withdrawals are stunning: somewhere north of $600 billion a year, according to one estimate in a recent study by the RAND Corp.
In the financial services industry, attacks on interbank transfers, card processing, ATM management, e-banking and payment gateways remain among the biggest current threats, according to the recent “Bank Robberies in the Digital Age” report from Positive Technologies, a cybersecurity firm:
“The range of targets is broad,” states the report. “If intruders have the necessary knowledge and technical means, access to such systems can bring them more revenue than fraud against bank customers. To steal money, criminals need to penetrate the bank’s infrastructure, which is usually quite well-guarded. Nonetheless, criminals still manage to bypass all protection mechanisms, and the media continue to report new bank cyberattacks and thefts.”
Here are five growing problems experts say banks must come to grips with in 2019.
Ransomware
Ransomware is main attack method used by fraudsters, one cybersecurity expert told BAI. Toxic code gets injected into a computer system, takes it over and locks out the administrators until they pay a ransom.
“The single biggest threat to financial institutions over the past year has been ransomware,” said Jeremy Scott, global director, threat research for NTT Security. “Ransomware has become a lucrative business for the criminal enterprise because of the ease of the attack and relatively low overhead to return on investment.”
That return on investment is huge, Scott notes.
“(We’ve) observed a significant increase in ransomware attacks against financial institutions,” he says. “There are some reports out that estimate about $5 billion in damages for 2017 and expectations of that figure doubling over the next year.”
Executive impersonation
Ransomware is not the only major threat for financial institutions in 2019, Scott says.
In one email phishing scheme, fraudsters pose as high-level executives to get employees or customers to transfer funds and sensitive data. And that business email compromise continues to dog otherwise vigilant organizations, Scott says. The FBI estimates that overall, businesses lost $12 billion between 2013 and 2018 as a result of these impersonation schemes, according to Krebson Security.
One of the biggest examples was an attack on an international money transfer organization based in California called Xoom, a PayPal service.
Xoom, according to the Infosec Institute, reported an incident where spoofed emails were sent to the company’s finance department. This resulted in the transfer of $30.8 million in corporate cash to fraudulent overseas accounts. The CFO resigned, and the company’s audit committee authorized an independent investigation by outside advisors. The company has implemented additional internal procedures, and federal law enforcement authorities are actively pursuing a multi-agency criminal investigation.
The fallout hurt financially in another way: Company stock dipped 14 percent, a loss of about $31 million.
Third-party access
Another concern for financial institutions are third-party vendors who have access to their digital domains.
“With the recent news on supply chain manipulation, this is a threat that the financial industry needs to pay attention to,” Scott says. “It’s important for financial institutions to extend their risk management program to their third-party vendors. Understanding the hardware and software risks of the vendor solutions will allow the financial institution’s decision makers to make informed decisions on the institutions network security, posture and risk.”
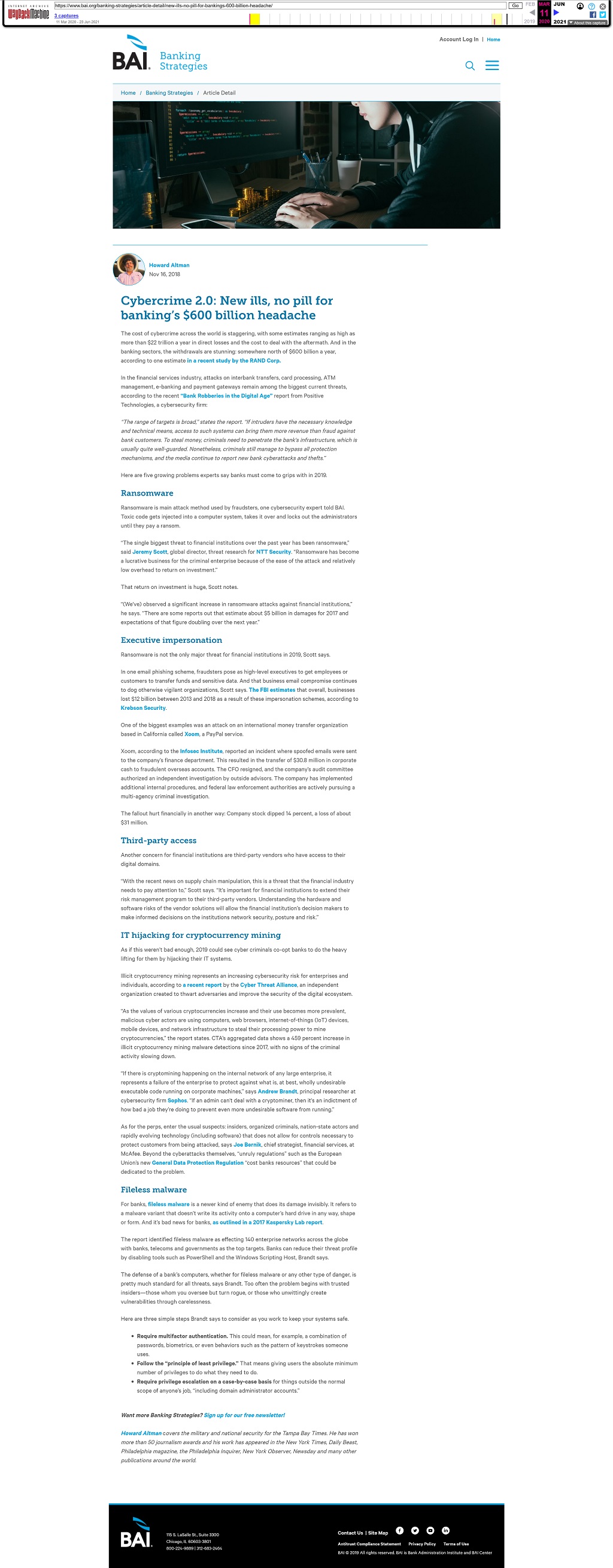
IT hijacking for cryptocurrency mining
As if this weren’t bad enough, 2019 could see cyber criminals co-opt banks to do the heavy lifting for them by hijacking their IT systems.
Illicit cryptocurrency mining represents an increasing cybersecurity risk for enterprises and individuals, according to a recent report by the Cyber Threat Alliance, an independent organization created to thwart adversaries and improve the security of the digital ecosystem.
“As the values of various cryptocurrencies increase and their use becomes more prevalent, malicious cyber actors are using computers, web browsers, internet-of-things (IoT) devices, mobile devices, and network infrastructure to steal their processing power to mine cryptocurrencies,” the report states. CTA’s aggregated data shows a 459 percent increase in illicit cryptocurrency mining malware detections since 2017, with no signs of the criminal activity slowing down.
“If there is cryptomining happening on the internal network of any large enterprise, it represents a failure of the enterprise to protect against what is, at best, wholly undesirable executable code running on corporate machines,” says Andrew Brandt, principal researcher at cybersecurity firm Sophos. “If an admin can’t deal with a cryptominer, then it’s an indictment of how bad a job they’re doing to prevent even more undesirable software from running.”
As for the perps, enter the usual suspects: insiders, organized criminals, nation-state actors and rapidly evolving technology (including software) that does not allow for controls necessary to protect customers from being attacked, says Joe Bernik, chief strategist, financial services, at McAfee. Beyond the cyberattacks themselves, “unruly regulations” such as the European Union’s new General Data Protection Regulation “cost banks resources” that could be dedicated to the problem.
Fileless malware
For banks, fileless malware is a newer kind of enemy that does its damage invisibly. It refers to a malware variant that doesn’t write its activity onto a computer’s hard drive in any way, shape or form. And it’s bad news for banks, as outlined in a 2017 Kaspersky Lab report.
The report identified fileless malware as effecting 140 enterprise networks across the globe with banks, telecoms and governments as the top targets. Banks can reduce their threat profile by disabling tools such as PowerShell and the Windows Scripting Host, Brandt says.
The defense of a bank’s computers, whether for fileless malware or any other type of danger, is pretty much standard for all threats, says Brandt. Too often the problem begins with trusted insiders—those whom you oversee but turn rogue, or those who unwittingly create vulnerabilities through carelessness.
Here are three simple steps Brandt says to consider as you work to keep your systems safe.
- Require multifactor authentication. This could mean, for example, a combination of passwords, biometrics, or even behaviors such as the pattern of keystrokes someone uses.
- Follow the “principle of least privilege.” That means giving users the absolute minimum number of privileges to do what they need to do.
- Require privilege escalation on a case-by-case basis for things outside the normal scope of anyone’s job, “including domain administrator accounts.”
- BAI: https://www.bai.org/banking-strategies/article-detail/new-ills-no-pill-for-bankings-600-billion-headache/
- Internet Archive: https://web.archive.org/web/20200311110918/https://www.bai.org/banking-strategies/article-detail/new-ills-no-pill-for-bankings-600-billion-headache/