News / Public Safety
Tweets posted from Buckhorn’s account include threats against Tampa International Airport and others along with racist and pornographic images.
By Howard Altman / Tampa Bay Times / February 21, 2019
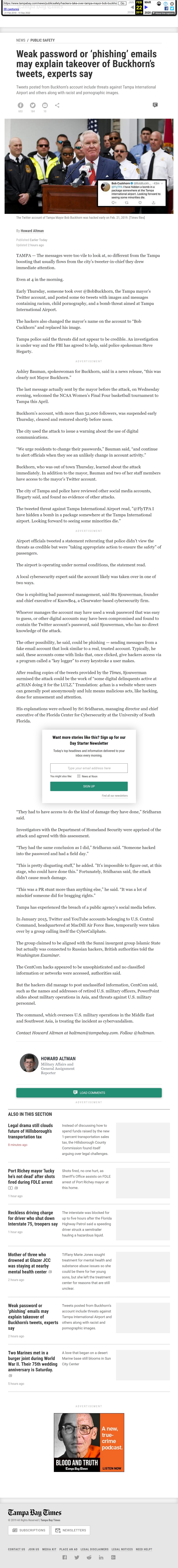
PHOTO: The Twitter account of Tampa Mayor Bob Buckhorn was hacked early on Feb. 21, 2019. (Times files)
TAMPA — The messages were too vile to look at, so different from the Tampa boosting that usually flows from the city’s tweeter-in-chief they drew immediate attention.
Even at 4 in the morning.
Early Thursday, someone took over @BobBuckhorn, the Tampa mayor’s Twitter account, and posted some 60 tweets with images and messages containing racism, child pornography, and a bomb threat aimed at Tampa International Airport.
The hackers also changed the mayor’s name on the account to “Bob Cuckhorn” and replaced his image.
Tampa police said the threats did not appear to be credible. An investigation is under way and the FBI has agreed to help, said police spokesman Steve Hegarty.
Ashley Bauman, spokeswoman for Buckhorn, said in a news release, “this was clearly not Mayor Buckhorn.”
The last message actually sent by the mayor before the attack, on Wednesday evening, welcomed the NCAA Women’s Final Four basketball tournament to Tampa this April.
Buckhorn’s account, with more than 52,000 followers, was suspended early Thursday, cleared and restored shortly before noon.
The city used the attack to issue a warning about the use of digital communications.
“We urge residents to change their passwords,” Bauman said, “and continue to alert officials when they see an unlikely change in account activity.”
Buckhorn, who was out of town Thursday, learned about the attack immediately. In addition to the mayor, Bauman and two of her staff members have access to the mayor’s Twitter account.
The city of Tampa and police have reviewed other social media accounts, Hegarty said, and found no evidence of other attacks.
The tweeted threat against Tampa International Airport read, “@FlyTPA I have hidden a bomb in a package somewhere at the Tampa International airport. Looking forward to seeing some minorities die.”
Airport officials tweeted a statement reiterating that police didn’t view the threats as credible but were “taking appropriate action to ensure the safety” of passengers.
The airport is operating under normal conditions, the statement read.
A local cybersecurity expert said the account likely was taken over in one of two ways.
One is exploiting bad password management, said Stu Sjouwerman, founder and chief executive of KnowBe4, a Clearwater-based cybersecurity firm.
Whoever manages the account may have used a weak password that was easy to guess, or other digital accounts may have been compromised and found to contain the Twitter account’s password, said Sjouwerman, who has no direct knowledge of the attack.
The other possibility, he said, could be phishing — sending messages from a fake email account that look similar to a real, trusted account. Typically, he said, these accounts come with links that, once clicked, give hackers access via a program called a “key logger” to every keystroke a user makes.
After reading copies of the tweets provided by the Times, Sjouwerman surmised the attack could be the work of “some digital delinquents active at 4CHAN doing it for the LULZ.” Translation: 4chan is a website where users can generally post anonymously and lulz means malicious acts, like hacking, done for amusement and attention.
His explanations were echoed by Sri Sridharan, managing director and chief executive of the Florida Center for Cybersecurity at the University of South Florida.
“They had to have access to do the kind of damage they have done,” Sridharan said.
Investigators with the Department of Homeland Security were apprised of the attack and agreed with this assessment.
“They had the same conclusion as I did,” Sridharan said. “Someone hacked into the password and had a field day.”
“This is pretty disgusting stuff,” he added. “It’s impossible to figure out, at this stage, who could have done this.” Fortunately, Sridharan said, the attack didn’t cause much damage.
“This was a PR stunt more than anything else,” he said. “It was a lot of mischief someone did for bragging rights.”
Tampa has experienced the breach of a public agency’s social media before.
In January 2015, Twitter and YouTube accounts belonging to U.S. Central Command, headquartered at MacDill Air Force Base, temporarily were taken over by a group calling itself the CyberCaliphate.
The group claimed to be aligned with the Sunni insurgent group Islamic State but actually was connected to Russian hackers, British authorities told the Washington Examiner.
The CentCom hacks appeared to be unsophisticated and no classified information or networks were accessed, authorities said.
But the hackers did manage to post unclassified information, CentCom said, such as the names and addresses of retired U.S. military officers, PowerPoint slides about military operations in Asia, and threats against U.S. military personnel.
The command, which oversees U.S. military operations in the Middle East and Southwest Asia, is treating the incident as cybervandalism.
Wayback image